## When was the last time you updated the firmware on your home WiFi router?
## The "S" in IoT stands for "Security".
[](https://owasp.org)
[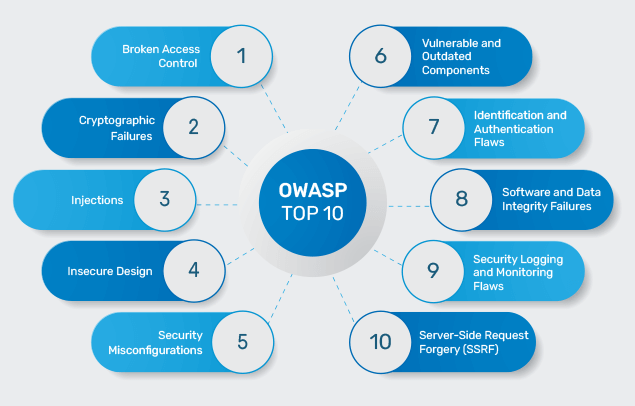](https://owasp.org/www-project-top-ten/)
notes:
* https://blog.omnetworks.com.np/owasp-top-10-understanding-the-most-critical-application-security-risks/
[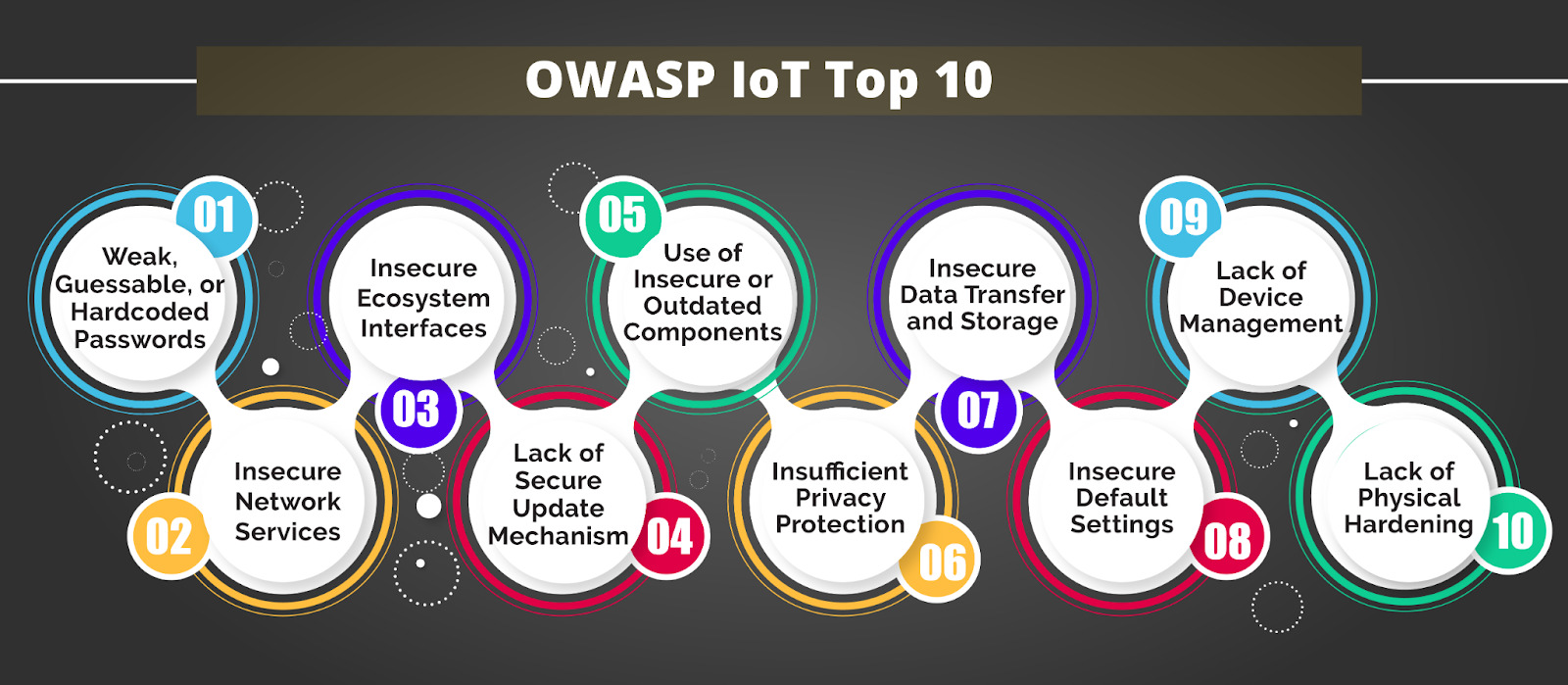](https://wiki.owasp.org/index.php/OWASP_Internet_of_Things_Project#tab=IoT_Top_10)
notes:
* https://www.appsealing.com/owasp-iot-top-10/
### #1 Weak, guessable or hard coded passwords
> Use of easily bruteforced, publicly available, or unchangeable credentials, including backdoors in firmware or client software that grants unauthorized access to deployed systems.
[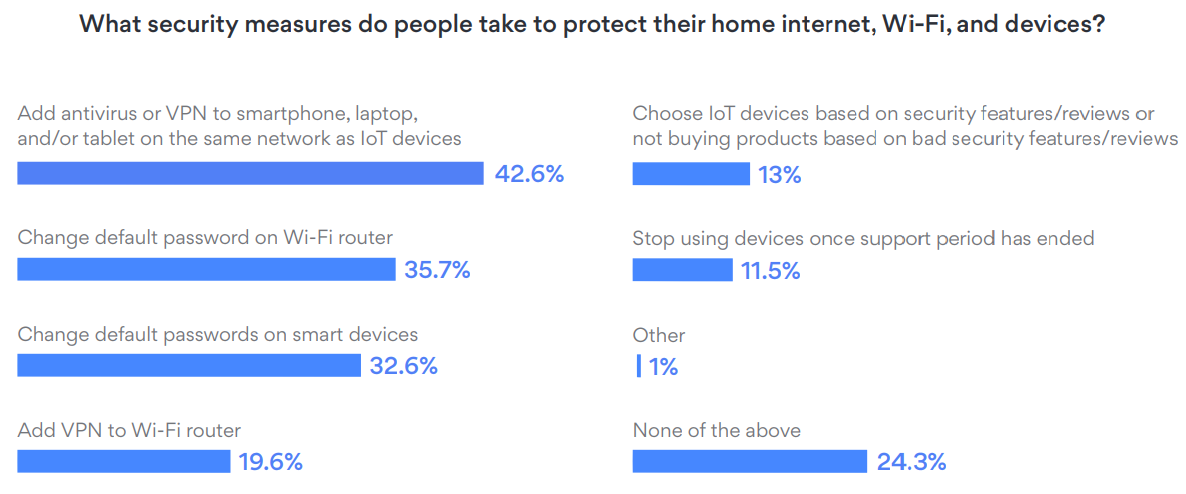](https://s1.nordcdn.com/nord/misc/0.42.0/vpn/brand/your-smart-devices-put-you-at-risk.pdf)
## [defpass.com](https://defpass.com/)
[](https://nordvpn.com/blog/baby-monitor-iot-hacking/)
[Hacker terrorizes family by hijacking baby monitor](https://nordvpn.com/blog/baby-monitor-iot-hacking/)
### #2 Insecure network services
> Unneeded or insecure network services running on the device itself, especially those exposed to the internet, that compromise the confidentiality, integrity/authenticity, or availability of information or allow unauthorized remote control...
```
$ nmap 192.168.1.1
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-03 18:51 CET
Nmap scan report for 192.168.1.1
Host is up (0.00057s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.15 seconds
```
### #3 Insecure ecosystem interfaces
> Insecure web, backend API, cloud, or mobile interfaces in the ecosystem outside of the device that allows compromise of the device or its related components. Common issues include a lack of authentication/authorization, lacking or weak encryption, and a lack of input and output filtering.
[](https://owasp.org/www-project-top-ten/)
notes:
* https://blog.omnetworks.com.np/owasp-top-10-understanding-the-most-critical-application-security-risks/
### #4 Lack of secure update mechanisms
> Lack of ability to securely update the device. This includes lack of firmware validation on device, lack of secure delivery (un-encrypted in transit), lack of anti-rollback mechanisms, and lack of notifications of security changes due to updates.

[AEG combi microwave unusable after update: device thinks it is a steam oven](https://taketonews.com/aeg-combi-microwave-unusable-after-update-device-thinks-it-is-a-steam-oven/) (March, 2022)
### #5 Use of insecure or outdated components
> Use of deprecated or insecure software components/libraries that could allow the device to be compromised. This includes insecure customization of operating system platforms, and the use of third-party software or hardware components from a compromised supply chain.
### #6 Insufficient privacy protection
### #7 Insecure data transfer and storage
### #8 Lack of device management
### #9 Insecure default settings
notes:
* https://www.reversinglabs.com/blog/mirai-botnet-continues-to-plague-iot-space
### #10 Lack of physical hardening